January 06, 2021

Setup Github SSH access from Jenkins
Stop authenticating with plain passwords
I recently enabled 2FA in my Github account which caused Jenkins to stop deploying my personal apps. This was expected because I was authenticating with plain credentials from Jenkins. Here’s how I changed my pipelines to authenticate with SSH keys instead.
- Get your server’s default SSH public key. In my case, Jenkins runs under the
jenkinsuser.
$ su - jenkins
$ cat ~/.ssh/id_rsa.pubCopy the content in your clipboard.
- Go to your Github account. Visit “SSH and GPG keys”.
- Click on “New SSH key”. Set Title to Jenkins SSH. Paste your key in the Key textarea.
- Now go to your Jenkins and visit “Credentials”.
- Click the “(global)” link.
- Click on “Add Credentials”.
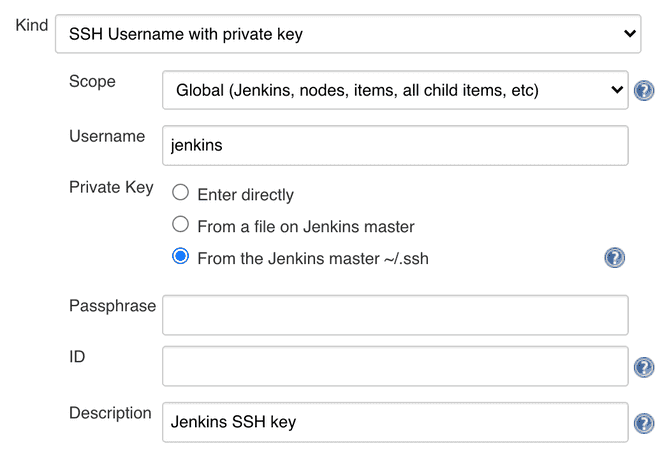
- Use the following values for each field:
- Kind: SSH Username with private key
- Scope: Global (Jenkins, nodes, items, all child items, etc)
- Username: jenkins
- Private key: From the Jenkins master ~/.ssh
- Description: Jenkins SSH key
- Hit “OK” and go back.
- Grab the ID of the recently created credentials.
- Use the new ID in your pipeline script. Here’s what my script looks like. Notice how I use the new credential’s ID in the property credentialsId:
#!/usr/bin/env groovy
node {
def app
stage("Clone") {
git branch: 'master',
credentialsId: '13171411-1a23-5e67-a8e9-f11e22221ec7',
url: 'git@github.com:caroso1222/carlos-roso-gatsby.git'
}
stage("Build") {
app = docker.build("caroso1222/carlos-roso-gatsby")
}
stage("Deploy") {
...
}
}There you have it. You’re good to build your pipelines in a real secure way.

I'm Carlos Roso. I'm a Production Engineer at Meta. Former SDE at Amazon. Ex digital nomad at Toptal and Crossover. In love with open source and design.
More about me